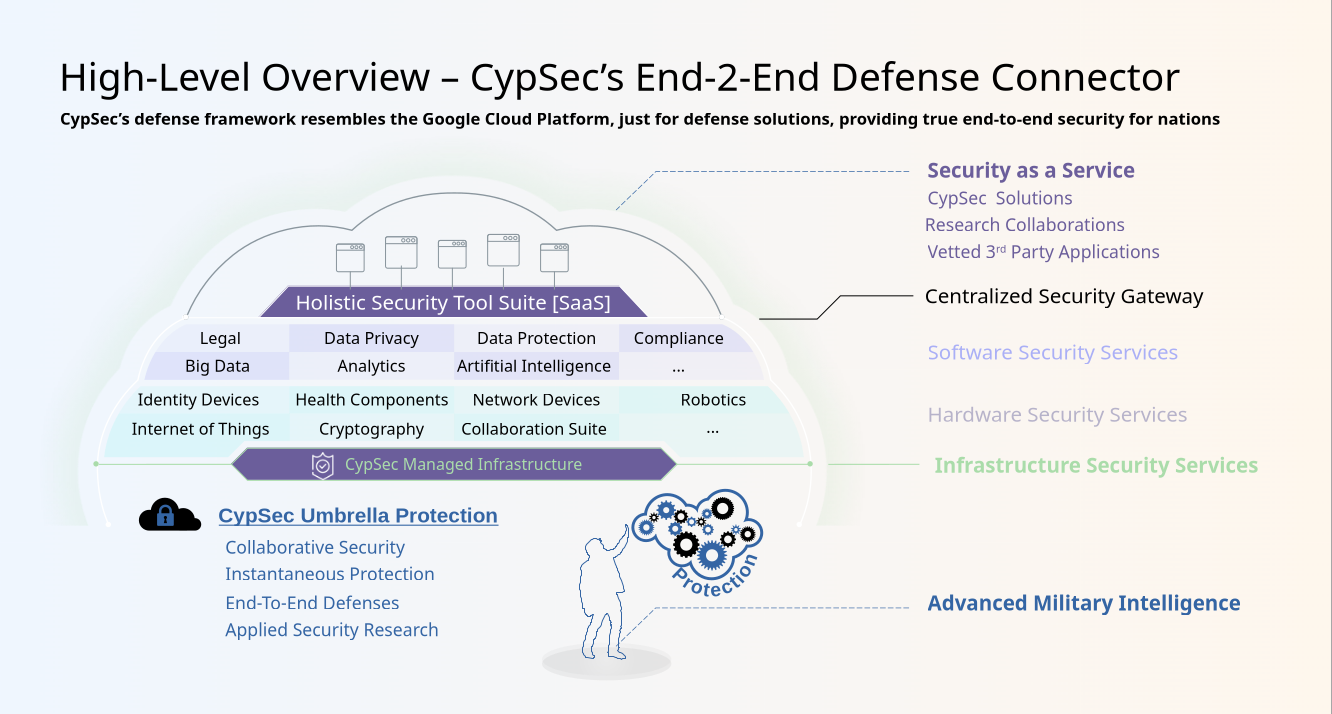
A Holistic Defense Framework That Transforms
Nation-states across the world are facing a generational shift in security challenges. Modern threats no longer emerge solely from conventional warfare. Instead, they now evolve within digital shadows, targeting vital institutions, critical infrastructure, and the very sovereignty of a nation. As governments digitize, adversaries adapt: foreign intelligence services, cyber-mercenaries, criminal syndicates, and insurgent groups are leveraging vulnerabilities in physical and digital systems to compromise defense integrity and civilian stability alike.
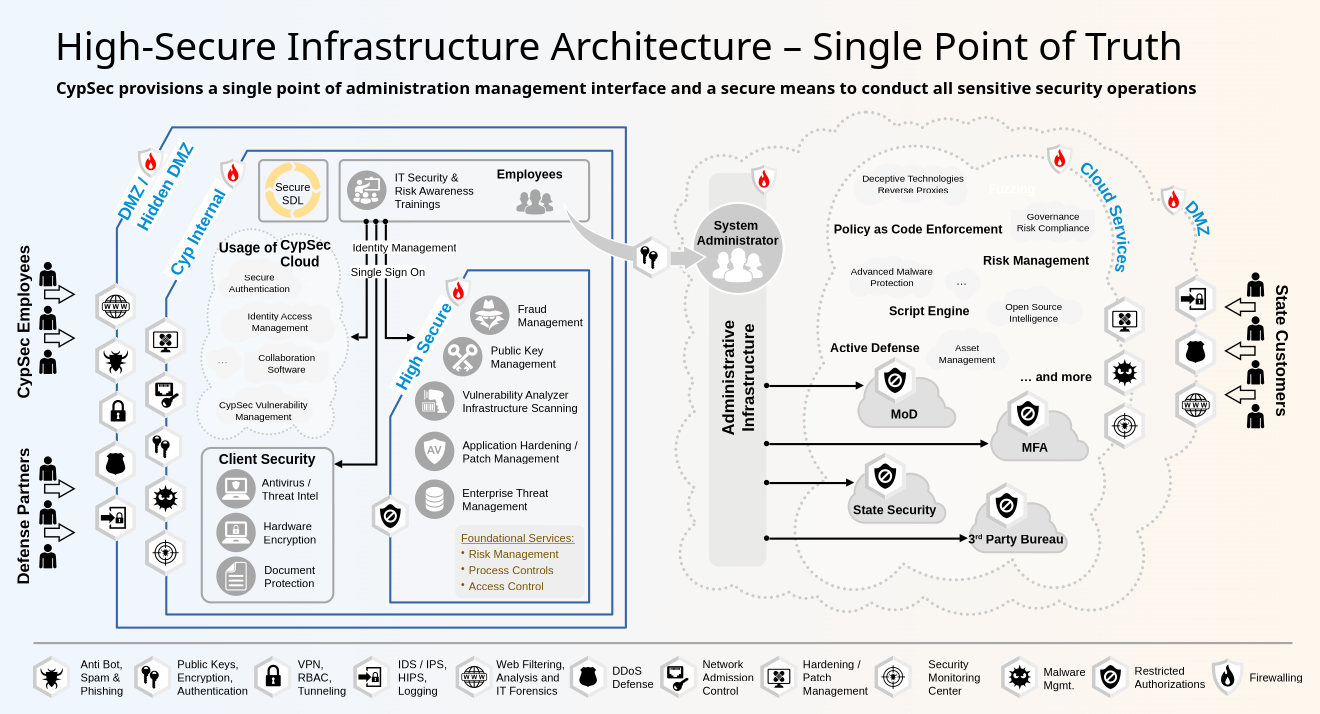
CypSec delivers a sovereignty-first defense platform tailored to states operating in complex threat environments with limited resources. Designed for deployment across defense, intelligence, and civil sectors, it enables full-spectrum national cyber resilience, independent of foreign cloud infrastructure or opaque technologies. The platform integrates secure communications, offensive and defensive cybersecurity capabilities, governance frameworks, deception technologies, and AI-assisted threat analysis to support both real-time incident response and long-term strategic planning. Its architecture ensures operational autonomy, scalability, and interoperability, offering governments a future-proof foundation for digital defense and national security.
Secure Infrastructure
Utilizing proactive detection and response security measures to neutralize potential risks and security incidents before they escalate.
14 Services
Secure Governance
Delivering insights and automated risk management solutions to navigate complex legal landscapes while minimizing exposure.
5 Services
Secure Collaboration
Enabling secure communication and seamless project management through end-to-end encrypted channels and privacy-centric features.
3 Services
Modular Defense Architecture for Sovereign Deployment
Built for strategic flexibility, CypSec's modular capabilities empower states to compose their own national cyber defense architecture, aligned with national priorities, infrastructure maturity, and strategic autonomy. Each module operates independently or within an integrated stack, including secure communications, adaptive threat intelligence, behavioral risk modeling, and mission-specific countermeasures such as deception and exploit containment. This design allows governments to strengthen their digital infrastructure incrementally, minimizing reliance on foreign platforms or rigid procurement cycles.
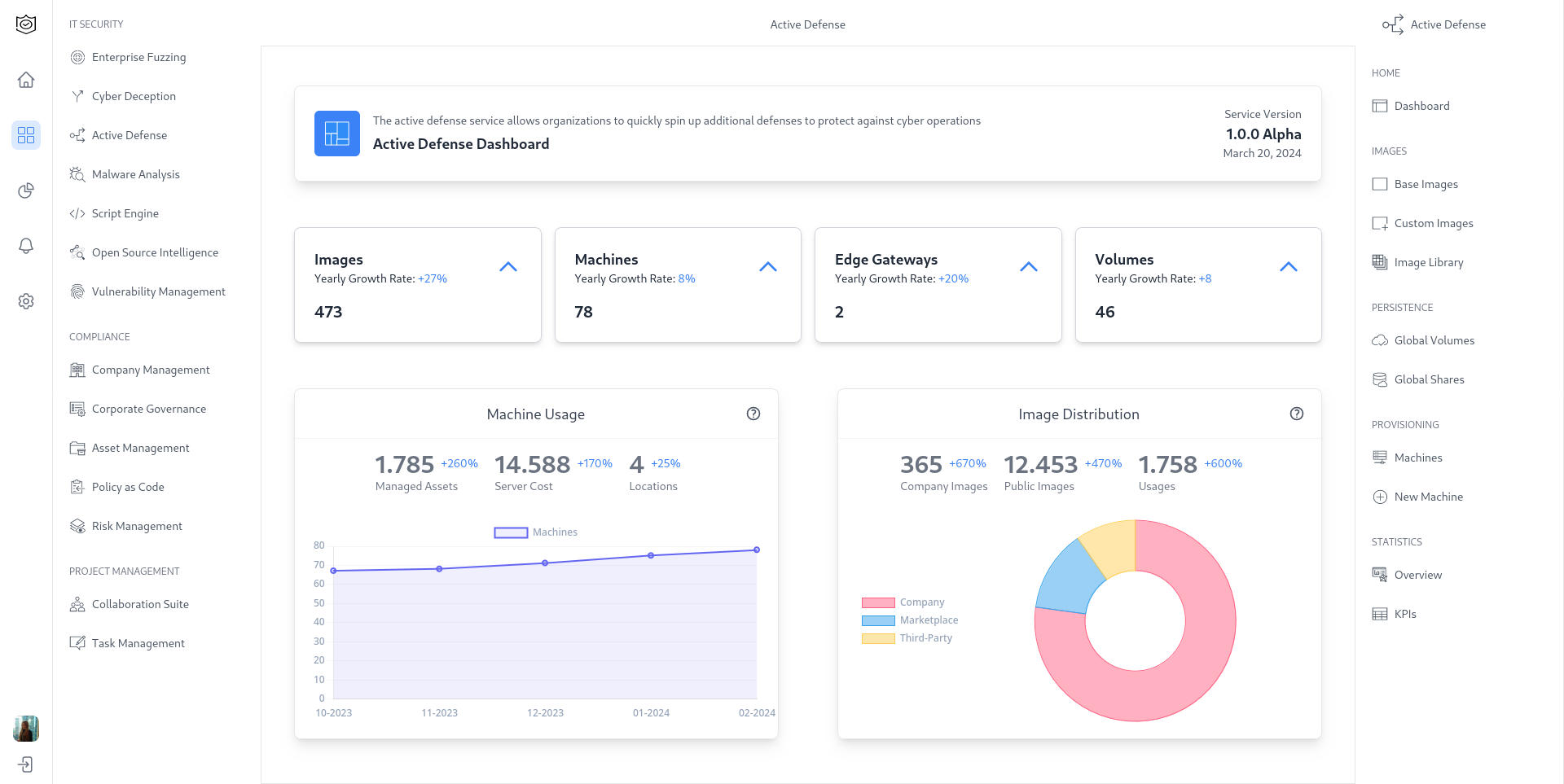
Active Defense
- AI algorithms rank vulnerabilities by their potential impact and exploitability.
- Threat intelligence is combined with internal system data for informed decision-making.
- Reducing false positives, allowing teams to remediate high-risk vulnerabilities faster.
Advantages for Governments and Law Enforcement
CypSec delivers a vertically integrated, on-premises security stack for national use. Our systems are designed to integrate directly with existing ministries of defense, intelligence, and infrastructure without reliance on third-party SaaS providers or Western intelligence-linked security vendors.
Offensive Cyber Capabilities
Offensive Cyber Capabilities for National Defense
As part of a coherent doctrine, CypSec provides payload engineering, in-situ testing environments, and real-time adversary simulation, fully under national control. Developed in collaboration with seasoned experts and applied researchers, these modules integrate with existing command infrastructure and are deployable within secure defense environments, including air-gapped networks and classified domains. Fully utilizing artificial intelligence, adaptive scripting engines, and signal intelligence integration, states can proactively engage with digital threats, disrupt hostile operations, and support kinetic operations with precision cyber effects.
Offensive capabilities are not deployed in isolation. They form part of a coherent doctrine aligned with conventional and hybrid warfare strategies. Modules include payload development frameworks, vulnerability research platforms, custom exploit orchestration, and red teaming environments, and are all operating under full national control. These systems enable mission-specific targeting, cyber reconnaissance, and simulated adversary engagement for both training and real-world operations. Combined with CypSec's secure communications and deception technologies, states gain the ability to shape digital battlefields on their own terms before adversaries do.
150+
Independent Security Experts
30+
Defense Modules
5.5 Years
Research and Development
100%
Architected for Foreign Independence
Redefining Cybersecurity Through Innovation
Modern national defense demands a cybersecurity architecture that is not only comprehensive but deeply interoperable across operational layers. CypSec's platform delivers an end-to-end defense ecosystem by fusing signal intelligence, behavioral analysis, and cryptographic assurance within a single modular framework. From the initial ingress point, starting at compromised devices, external payloads, or insider actions, every packet and process is tracked against dynamic baselines derived from real-time telemetry. Threat modeling is continuously updated through AI-assisted correlations across modules, allowing early identification of lateral movement, protocol abuse, or anomalies in encrypted traffic. Rather than relying on siloed alerts, the system constructs a convergent threat narrative that reflects the adversary's intent, infrastructure, and tactics.
Operational control is reinforced by a zero-trust communication layer, decentralized command capabilities, and deeply integrated deception environments. Each node within the infrastructure, including cloud-less secure enclaves or edge devices in critical infrastructure, is equipped with tamper-proof integrity monitoring and context-aware response logic. Malware is not just analyzed. It's emulated in isolated dynamic sandboxes that track memory-level behavior, system call chains, and binary evasion patterns. Intelligence gathered from these events feeds back into mission-specific countermeasures, such as adaptive access control policies or strategic misdirection deployments. The result is a closed-loop defense ecosystem where insight, attribution, and preemption converge, transforming cybersecurity from a reactive posture to a sovereign operational asset.
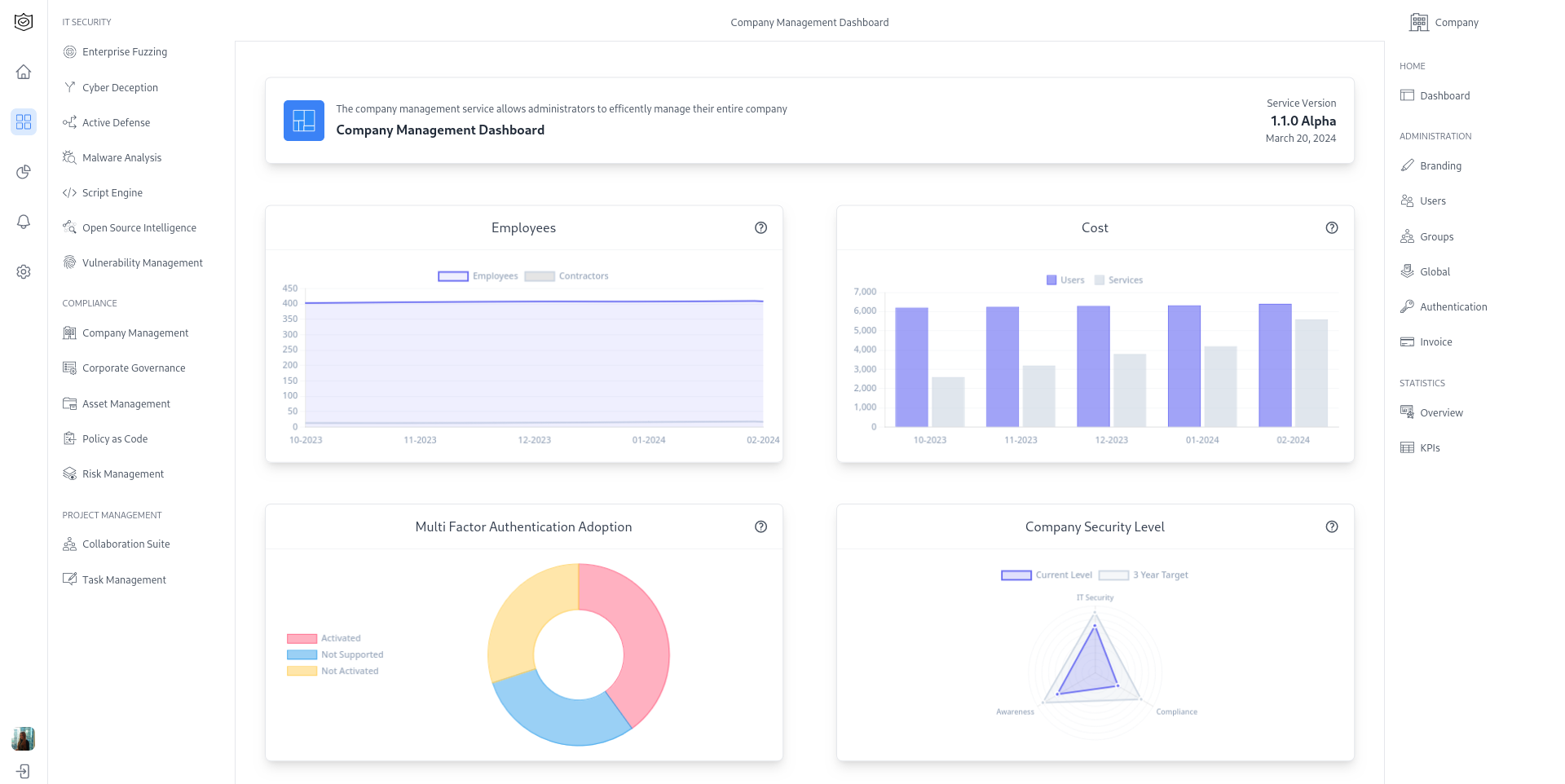
Integrated Civil-Military Security Ecosystem
CypSec bridges the gap between civil resilience and military readiness through an interoperable architecture that operates across ministries, command centers, and critical national infrastructure, while maintaining protocol consistency, secured identity layers, and shared threat intelligence frameworks. Both civil and defense sectors can act with unified coordination while preserving role-based autonomy. This approach benefits from a consistent foundation of integrity, operational clarity, and full national oversight. Tactical command platforms integrate seamlessly with national-scale governance solutions, while civilian digital services inherit hardened cybersecurity by design. This interconnectivity simplifies operations under pressure and empowers states to treat cyber resilience as a strategic continuum, not a siloed function.
Click to Zoom
Human Intelligence
Operationalized insight through a trusted partner network of ethical hackers, red-team specialists, and academic researchers. Enables active threat simulation and predictive defense modeling.
Click to Zoom
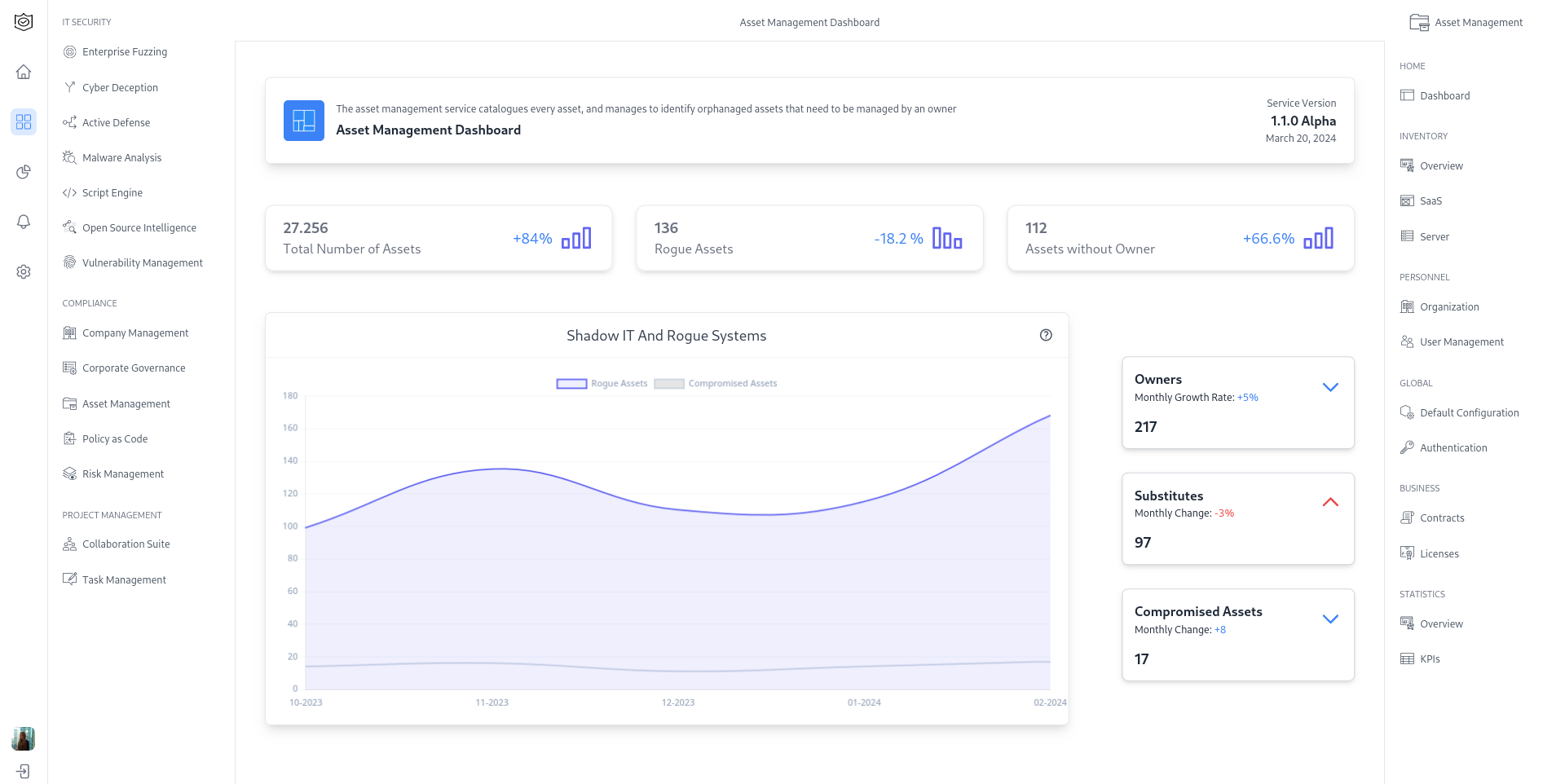
Secure Infrastructure
End-to-end hardened environments, ranging from on-premise secure enclaves to air-gapped command systems, to ensure autonomy, resilience, and physical/digital tamper resistance at every layer.
Click to Zoom
Secure Governance
Policy-driven defense workflows with transparent audit trails, integrated compliance modules, and automated enforcement capabilities for ministries, intelligence, and regulatory bodies alike.
Click to Zoom
Secure Collaboration
Encrypted, role-based communication and defense coordination across military, civil, and international partners. Includes secure project rooms, red-teaming labs, and compliant data exchange nodes.
System Advantage
Cross-sector interconnectivity ensures faster response, strategic clarity, and unified deterrence in both peacetime and crisis scenarios.
Return on Investment
Reduced breach costs, increased operational uptime, and national sovereignty over mission-critical assets without recurring vendor lock-in.
Real-World Impact of CypSec's Defense Solutions
To respond effectively to modern cyber threats, states require more than isolated firewalls or third-party monitoring services. They need a strategically coordinated, nationally sovereign cybersecurity infrastructure. CypSec enables this through flexible work packages tailored to diverse governmental architectures: centralized command-grid structures for ministries of defense, decentralized regional nodes for federated states, or integrated civil-defense platforms that span across ministries of interior, telecom, health, and energy. These deployments are instrumental for efficient policy making.
Each model establishes national command over digital terrain, creating the visibility, control, and response capabilities needed to detect, isolate, and neutralize threats in real time. With capabilities like behavior-driven intrusion detection, dynamic deception layers, sovereign malware analysis environments, and encrypted command platforms, governments gain the operational maturity to not only defend their infrastructure but to establish cyber deterrence. This shifts the balance: hostile actors no longer encounter fragmented, reactive defenses, but a sovereign digital posture with the ability to attribute, respond, and escalate when necessary, on terms defined by the state itself.
Decentralized Resilience Nodes
Regional data centers tied into a national security operations center, supporting local municipalities and ministries.
Civil-Defense Integrated Platform
Joint deployment between interior, telecom, energy, and health sectors with crisis response modules.
Strategic Command Grid
Full deployment in MoD or intelligence HQs with integration across border control, CNI, and armed forces.
"True sovereignty in the digital age means building systems that not only protect, but adapt, respond, and endure. Instead of selling cybersecurity, we are enabling effective statecraft."
- Chief Executive Officer at CypSec, Daria FediayCypSec's defense services are not transactional, nor are they built around reactive incident management. Instead, they are structured as long-term operational engagements that embed security architecture into the fabric of a customer's mission. This could involve national infrastructure, defense logistics, or civilian-critical digital systems. The offering moves beyond perimeter control or compliance checks and into real-time threat behavior modeling, adversarial simulation, and resilience engineering at scale. Our clients do not purchase protection. Instead, they gain access to doctrine-backed operational capabilities, integration with live intelligence streams, and co-developed defense modules tailored to specific threat topologies. Every component of the service, from decision-layer telemetry to kill-chain mapping, is designed to reduce the asymmetry between attacker intent and defender readiness. What we deliver is not coverage, but command of the defensive landscape.
CypSec's defense service operates as a modular, embedded unit that integrates directly into an organization's existing infrastructure and decision cycles. Each engagement begins with a full-spectrum threat audit and adversary modeling exercise, followed by deployment of custom monitoring logic and behavior-based detection agents. This is supported by continuous telemetry ingestion, anomaly clustering, and live-response readiness protocols. Partners are granted access to our security operations center backbone, which operates on a federated model to preserve local control while enabling joint situational awareness. Depending on the engagement scope, we also establish mission-specific war rooms, operational test environments, or classified simulation labs for advanced threat scenario rehearsal. Integration is never superficial: our teams work shoulder-to-shoulder with yours, aligning defensive capability to strategic objectives with technical and doctrinal depth.
CypSec's architecture is fully vendor-independent, audit-capable, and structurally sovereign. We do not embed third-party monitoring code, route telemetry through foreign jurisdictions, or rely on proprietary logic we cannot explain or control. Every system we deploy can be self-hosted, fully documented, and is designed to function autonomously within your existing operational security doctrine. Data governance remains entirely with the client. Our engagement model emphasizes mutual accountability: all detection logic, response playbooks, and decision-support tools are available in transparent form, subject to technical review and mission-specific modification. When a breach or critical anomaly occurs, our team does not simply notify. We investigate, contain, and neutralize threats in active coordination with your internal response units. Strategic accountability is not outsourced. It is embedded into every layer of our defensive design.
CypSec's defense offering is architected to operate under the assumption of persistent, multi-vector threats, including those posed by state-linked actors, advanced persistent threats, and coordinated disinformation or disruption campaigns. We do not operate under a “baseline normal” assumption. Instead, our systems continuously adapt through behavior feedback loops, red team adversarial simulations, and telemetry from high-fidelity threat emulation environments. Readiness is maintained through ongoing intelligence fusion, frequent system hardening, and deployment of preconfigured escalation protocols tied to operational risk thresholds. Our detection frameworks include low-signal anomaly identification, lateral movement tracking, and adversarial command structure inference. For critical infrastructure and defense-linked partners, we also support kinetic risk modeling, cyber-physical integration, and hybrid threat rehearsals. The goal is not simply to survive high-intensity environments, but to operate decisively within them.









